As an introduction to hardware hacking, I recently acquired a cheap Linux router. In this post we’ll take a look at how to find and interact with the UART (Universal Asynchronous Receiver-Transmitter) interface, demonstrating the first steps in reverse engineering the router. We’ll then dig a little deeper once a shell is established.


After opening the case, we can take a look at the PCB. Straight away we can locate the UART interface by its clearly labeled pins.

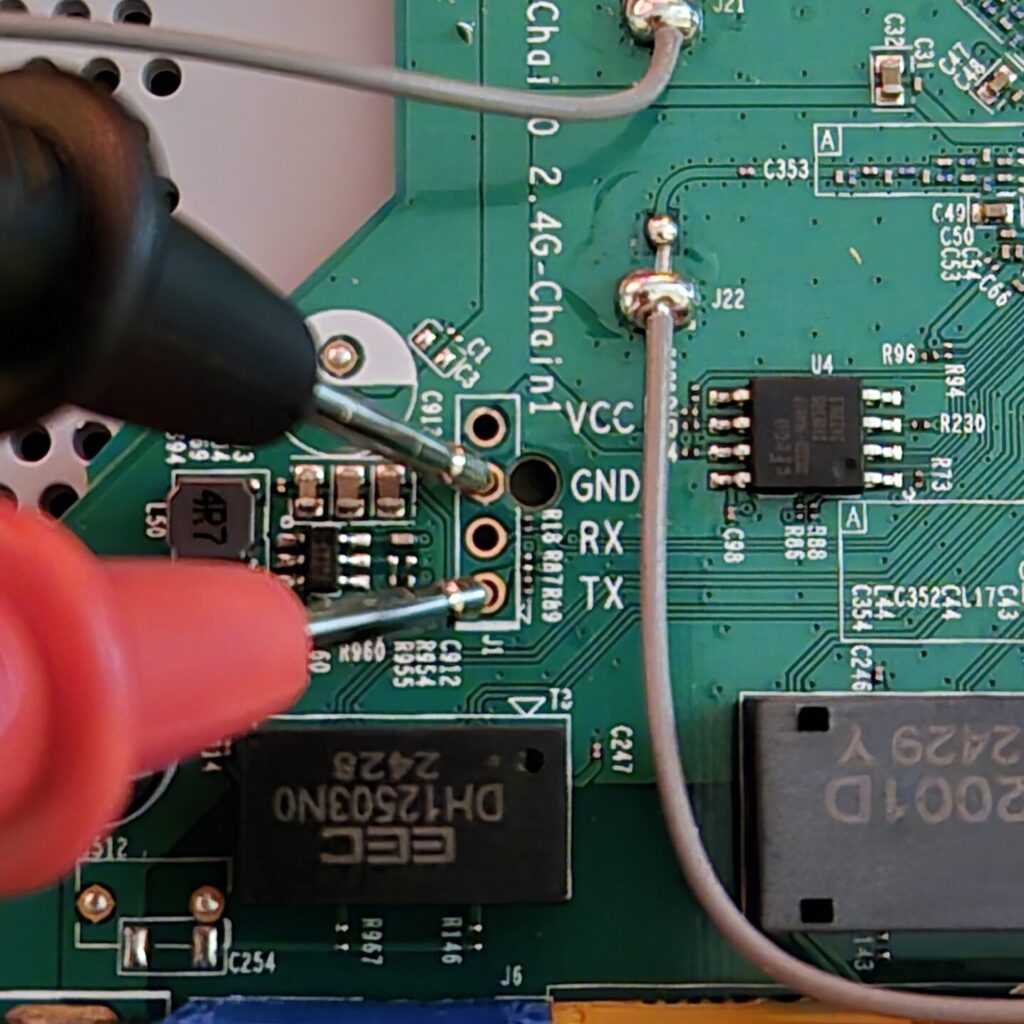
Even thought the pins are labeled in this case, we can verify that these are in fact the correct pins:
- VCC: Should be at a constant 3.3V or 5.0V when the device is powered on.
- GND: Can be checked using the continuity mode on the multimeter and another ground point on the PCB.
- TX: Is expected to fluctuate in voltage during the boot process (indicating data being sent sporadically).
- RX: Can be determined using the process of elimination as its the last remaining pin.
To make it easy to connect and interact with the UART interface, lets solder on some pins!
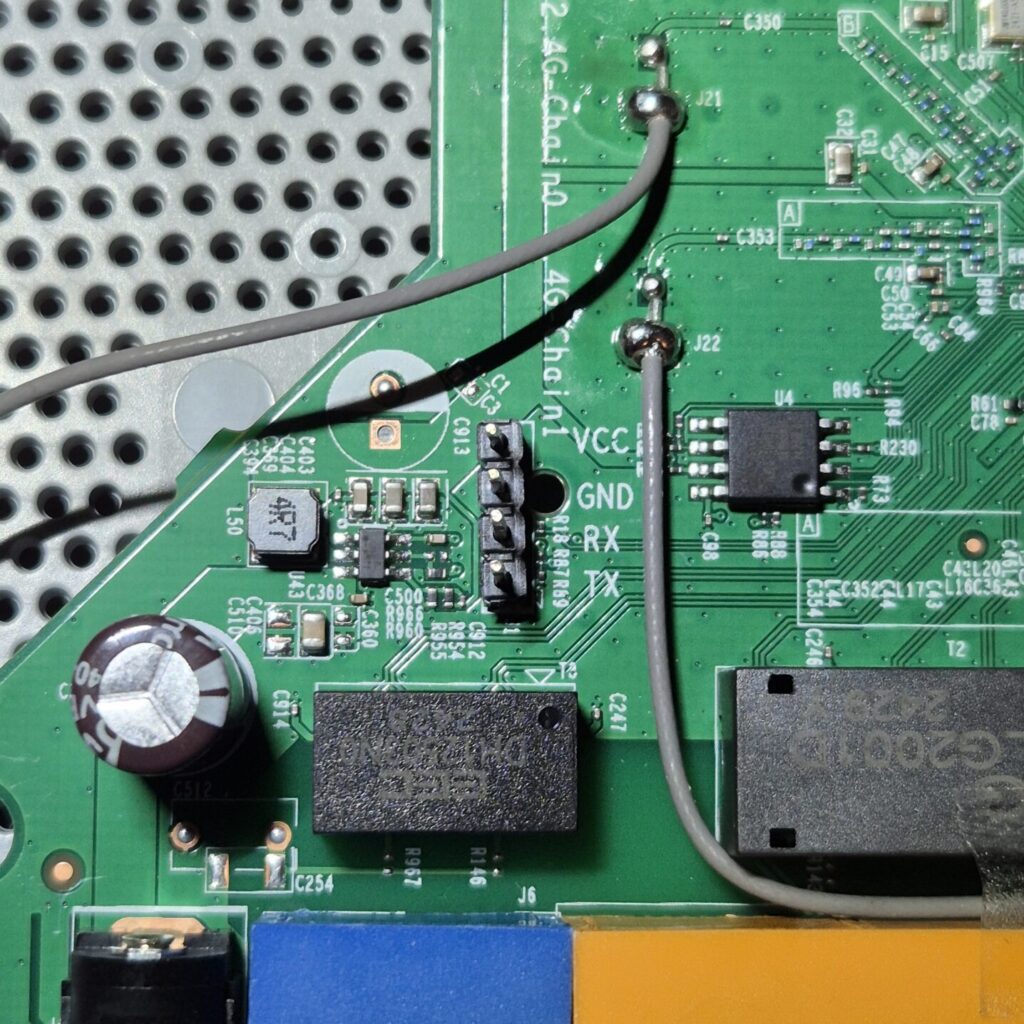
Using a USB to UART converter, we can connect to the pins on the PCB. The TX pin on the converter connects to the RX pin on the PCB, and the TX pin on the PCB connects to the RX pin on the converter. The VCC pin does not need to be connected as voltage to the UART interface will be supplied when the device is powered on.

Now, using a tool such as picocom we can connect to the serial console. The easiest way to determine which baud rate to use is to test the standard ones, the most common one is 115200. If the wrong baud rate is selected, the data received will look like gibberish.
$ picocom -b 115200 /dev/ttyUSB0Then we can power on the device and watch the boot log…
[04080B0E][04080B0F][7F7F0000][26263939][0026263A]
DU Setting Cal Done
U-Boot 1.1.3 (Aug 16 2022 - 16:03:05)
Board: Ralink APSoC DRAM: 32 MB
relocate_code Pointer at: 81fc0000
flash manufacture id: 1c, device id 70 16
Warning: un-recognized chip ID, please update bootloader!
============================================
Ralink UBoot Version: 4.3.0.0
--------------------------------------------
ASIC 7628_MP (Port5<->None)
DRAM component: 256 Mbits DDR, width 16
DRAM bus: 16 bit
Total memory: 32 MBytes
Flash component: SPI Flash
Date:Aug 16 2022 Time:16:03:05
============================================
icache: sets:512, ways:4, linesz:32 ,total:65536
dcache: sets:256, ways:4, linesz:32 ,total:32768
##### The CPU freq = 580 MHZ ####
estimate memory size =32 Mbytes
RESET MT7628 PHY!!!!!!
continue to starting system.
0
disable switch phyport...
3: System Boot system code via Flash.(0xbc010000)
do_bootm:argc=2, addr=0xbc010000
## Booting image at bc010000 ...
Uncompressing Kernel Image ... OK
No initrd
## Transferring control to Linux (at address 8000c150) ...
## Giving linux memsize in MB, 32
Starting kernel ...
LINUX started...
THIS IS ASIC
Linux version 2.6.36 (jenkins@sohoici) (gcc version 4.6.3 (Buildroot 2012.11.1) ) #1 Tue Aug 16 16:06:23 CST 2022
The CPU feqenuce set to 575 MHz
MIPS CPU sleep mode enabled.
CPU revision is: 00019655 (MIPS 24Kc)
Software DMA cache coherency
Determined physical RAM map:
memory: 02000000 @ 00000000 (usable)
Initrd not found or empty - disabling initrd
Zone PFN ranges:
Normal 0x00000000 -> 0x00002000
Movable zone start PFN for each node
early_node_map[1] active PFN ranges
0: 0x00000000 -> 0x00002000
Built 1 zonelists in Zone order, mobility grouping on. Total pages: 8128
Kernel command line: console=ttyS1,115200 root=/dev/mtdblock2
[...]…and then we get dropped right into a root shell! No login required for this device.
~ #
~ #
~ # echo $USER
rootFurther investigation
Looking at the password file, we can se that it contains the user ‘admin’ including its encrypted password.
~ # cat /etc/passwd
admin:$1$$iC.dUsGpxNNJGeOm1dFio/:0:0:root:/:/bin/sh
dropbear:x:500:500:dropbear:/var/dropbear:/bin/sh
nobody:*:0:0:nobody:/:/bin/shLet’s see if we can crack it using hashcat. Using the example hashes page on the hashcat wiki, we can identify which hash type is used by searching for the beginning of our hash and see if we find any similar one. We find that it uses md5crypt, which can be specified by selecting hash mode #500. We’ll start of by performing a dictionary attack, using the ‘rockyou.txt‘ wordlist as input.
┌──(kali㉿kali)-[~]
└─$ hashcat -m 500 password.txt /usr/share/wordlists/rockyou.txt
$1$$iC.dUsGpxNNJGeOm1dFio/:1234The password was cracked instantly, and turns out to be as simple as ‘1234’. Thereby, we have obtained the login credentials for this user, admin:1234.

